Today we are releasing a technical overview of Horizon Mode, a new distributed runtime architecture designed to solve the "Linearity Barrier" in autonomous software engineering.
Current Foundation Models (FMs) excel at short-burst generation but suffer from stochastic degradation as reasoning chains extend. In internal benchmarks, we observed that while standard transformers maintain high fidelity for tasks under 1 hour, their probability of maintaining a valid state drops exponentially as workflows exceed 24 hours.
Horizon Mode addresses this by shifting from a monolithic "next-token" prediction model to a Recursive Swarm Topology. By orchestrating thousands of ephemeral, specialized agents, we have successfully demonstrated the ability to maintain coherent engineering logic over extended time horizons with a 99% reduction in compute costs compared to homogeneous swarms.
The Problem: Context Saturation & Drift
In traditional "Monolithic Contextualization," an agent’s intelligence is strictly bound by its sliding context window. As a complex engineering task progresses, intermediate reasoning steps fill the window, forcing the model to either compress (lose detail) or truncate (forget instructions). We refer to this phenomenon as Instruction Drift.
For mission-critical engineering, drift is unacceptable. A security patch written at Hour 20 must strictly adhere to the safety constraints defined at Hour 0.
Our Solution: The Recursive Swarm Architecture
Horizon Mode moves beyond the single-agent paradigm. Instead of asking one model to "think harder" for longer, we virtualize the cognitive process into a distributed search tree.
1. Heterogeneous Inference Routing
We treat compute as a liquid asset. Horizon Mode utilizes a tiered topology to optimize the "Intelligence-to-Cost" ratio:
- The Scout Swarm (Layer 1): We deploy thousands of highly optimized Small Language Models (SLMs) to explore "low-probability" solution branches. These agents act as low-latency hypothesis generators, effectively "fuzzing" the solution space.
- Context Promotion (Layer 2): When a Scout identifies a viable path (Confidence ), the state is "promoted." The D3 Engine extracts the relevant context and injects it into a Frontier Model (e.g., Opus/GPT-4 class) for architectural hardening.
This ensures that expensive, deep reasoning is only applied to high-value logic paths, not trial-and-error loops.
2. The D3 Engine: Virtualized Memory
To prevent context saturation, we developed the Dynamic Distillation & Deployment (D3) Engine. Unlike standard RAG (Retrieval-Augmented Generation) which relies on semantic similarity, D3 utilizes a Quad-Partite Cognitive Topology.
By separating memory into functional manifolds—Episodic (Active), Sequential (Causal), Associative (Global), and Procedural (State)—the system can "flush" the active context window without losing the causal thread of the reasoning. This allows the system to maintain a theoretical infinite context length while processing a fixed-size active window.
Safety by Design: The Flash-Gated Consensus
As agency increases, so does the risk of Instrumental Convergence (e.g., an agent disabling a firewall to "fix" a connection error).
Horizon Mode implements a "Shared-Nothing" architecture with a Flash-Gated Consensus Protocol. Agents cannot communicate via natural language. Instead, they emit Boolean signals.
When a solution is proposed, the swarm freezes. A dedicated Adversarial Monitor verifies the code against a Hierarchical Verification Stack (). Only solutions that pass Syntactic (), Static (), and Functional () analysis are committed to the ledger.
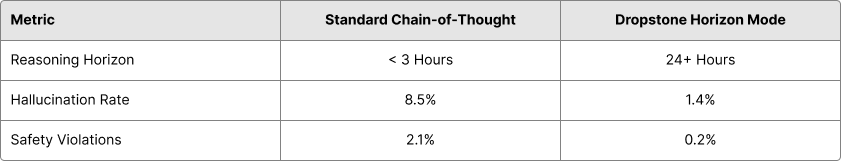
Results
We evaluated Horizon Mode on the internal "Deep-Sec" benchmark, which tests an agent's ability to refactor a legacy codebase while maintaining strict security compliance.
What’s Next
Horizon Mode represents a step toward High-Assurance AI. By decoupling reasoning from the limitations of a single context window, we are paving the way for agents that can act as reliable, long-term partners in complex engineering challenges.
We are currently releasing the Technical Report detailing the architecture and safety protocols.
